Introduction:
In the dynamic realm of telecommunications, the persistent menace of caller ID spoofing presents a formidable challenge, jeopardizing the integrity of communications worldwide. Addressing this threat head-on, the industry has introduced Stir/Shaken, a revolutionary technology poised to serve as the vanguard against such deceptive practices. This article delves into the intricacies of caller ID spoofing, explores the transformative potential of Stir/Shaken, and unveils Peeringhub.io's innovative approach to facilitating a seamless ACME implementation for Stir/Shaken certificate issuance.
Understanding Caller ID Spoofing:
Caller ID spoofing involves the deliberate manipulation of information displayed on a recipient's caller ID, creating a false aura of legitimacy. Employing an array of tactics including software applications and specialized equipment, scammers aim to falsify their identities and phone numbers, exposing unsuspecting individuals to risks such as financial losses, identity theft, and various forms of fraud.
The Implications of Caller ID Spoofing:
Caller ID spoofing poses significant risks, enabling malicious actors to impersonate trusted entities and coerce victims into divulging sensitive information. Beyond financial ramifications, this nefarious practice can lead to identity theft, persistent harassment, and involvement in illicit schemes. It is imperative to implement robust solutions to safeguard phone users against these deceptive tactics.
Harnessing Stir/Shaken to Counter Threats:
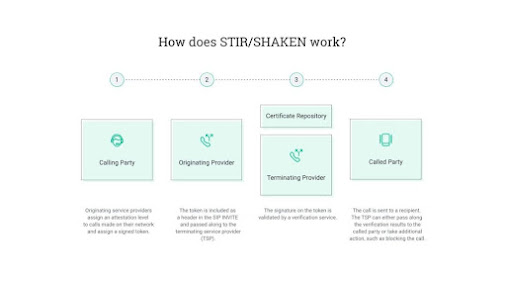
Stir/Shaken, shorthand for Secure Telephone Identity Revisited and Signature-based Handling of Asserted Information Using Tokens, offers a comprehensive framework engineered to authenticate and verify caller identity. This groundbreaking technology serves as a potent defense against caller ID spoofing by assigning a unique digital signature to each outgoing call.
The Stir/Shaken process entails the originating service provider generating a digital signature based on the caller's phone number and call timing. As the call traverses the telecom network and reaches the recipient's service provider, the signature undergoes meticulous validation to ensure alignment with the caller's details. Any deviations may trigger alerts for potential fraudulent activity or prompt call blocking.
Peeringhub.io: Leading ACME Implementation for Stir/Shaken Certificates:
Peeringhub.io stands at the forefront of telecom innovation, providing a comprehensive ACME implementation for the seamless issuance of Stir/Shaken certificates. Its state-of-the-art self-service desktop solution empowers carriers to request certificates directly from their PCs, streamlining the process for enhanced convenience and efficiency.
Self-Service Subscription for Unparalleled Control:
Peeringhub.io further elevates the Stir/Shaken implementation experience with its self-service subscription model. Service providers can effortlessly sign up online and manage their subscriptions via a fully automated web portal. This intuitive approach grants providers unmatched control over their Stir/Shaken implementation, ensuring a personalized and secure experience.
About Peeringhub.io:
Peeringhub.io is committed to simplifying telecom processes and offers a secure, user-friendly solution for Competitive Local Exchange Carriers (CLECs) seeking to automate Telephone Number (TN) management. Recognizing the significance of flexibility and customization, Peeringhub.io's product is tailored to accommodate each business's unique needs, fostering solutions that cater to individual requirements.
Conclusion:
In conclusion, Stir/Shaken emerges as a pivotal technology in the battle against caller ID spoofing, with Peeringhub.io leading the charge in innovation. Its dedication to providing a seamless ACME implementation and self-service subscription model empowers carriers to combat fraud effectively while maintaining control over their telecom operations. As the telecom landscape evolves, Peeringhub.io remains at the forefront, empowering businesses to navigate the complexities of telecommunications with confidence and security.

Post a Comment